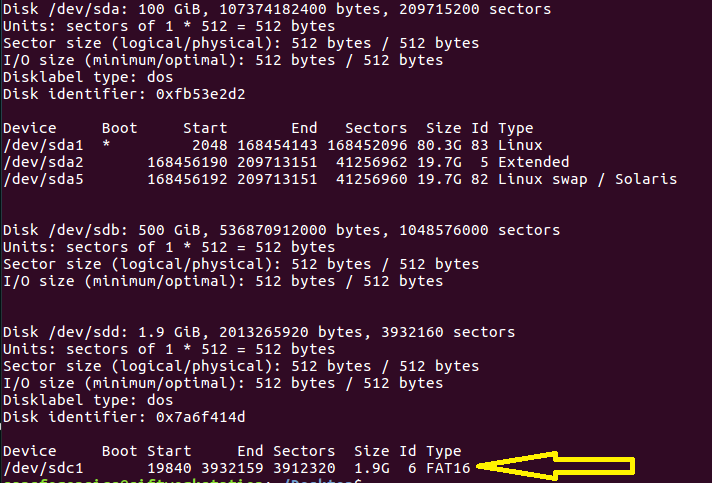
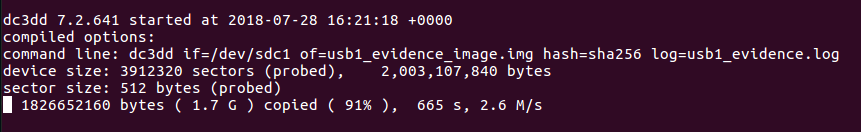
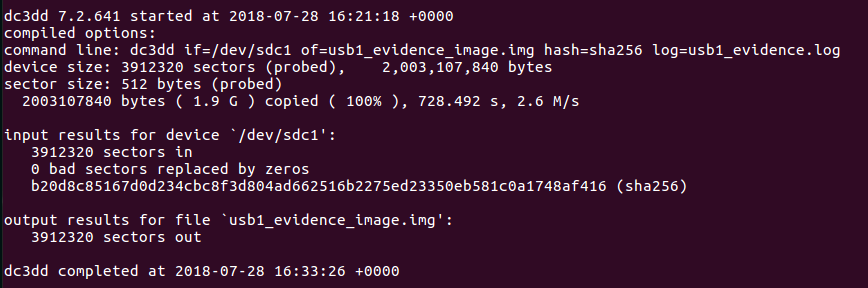
There are a lot of ways to determine when a Windows operating system have been installed on a machine. In this post you will find some examples.
The installation date is very important during a forensic invegation in order to quickly understand when a Windows operating system have been installed on the analyzed machine.
Please bare in mind, that on Windows 10, this date can refer to the last major update (e.g. creators update).
-
-
-
Extraction from Windows registry with Powershell:
It is possible to retrieve the date and the time directly from a registry which is:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\InstallDate
The value of the registry key “InstallDate” is expressed as UNIX time, in a few words, it displays the time in number of seconds since 1st Jan 1970.
You can obtain a readeable value with Powershell, writing:$date = Get-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\' | select -ExpandProperty InstallDate
The variable $date contains the installation datetime in UNIX time. In order to convert it into a human readable format in the same Powershell, you shall write:
(Get-Date "1970-01-01 00:00:00.000Z") + ([TimeSpan]::FromSeconds($date))
Now you have a human readable installation date time.
Requirement: Powershell
SO: Windows 7+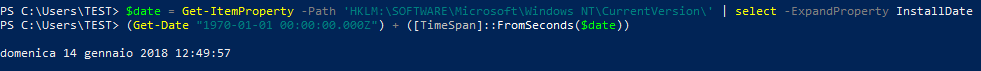
Extracting from Windows registry with Powershell -
Using systeminfo via CMD:
Systeminfo displays configuration information about a computer and its operating system, and also the Original Installation Date. To extract the installation date, open a cmd and type:
systeminfo | find /i "original"
Using the string “Original Install Date” please note that in order to find valid information, your OS language shall be English, otherwise you may not be able to find anything.
Requirement: cmd
SO: Windows XP+ -
Using WMI via Powershell:
It is also possible to extract the installation date and time with WMI, which stands for “Windows Management Instrumentation“. Open a powershell windows and write this command:
([WMI]'').ConvertToDateTime((Get-WmiObject Win32_OperatingSystem).InstallDate)
With this command, you will get the installation date in a human readable format.
Requirement: Powershell
SO: Windows 7+ -
Client side Cache Folder on Windows 10:
On Windows 10, all the methods listed before, could retrieve the date of the last major updates (e.g. creators update) and not the Original Installation date.
A nice way to find the closest thing to the original installation date on a Windows 10 system is to look at the “last write time” of the client side cache and you can do it by using powershell:Get-Item C:\Windows\CSC\
The “Last Write Time” is one of the closest things to the original installation date of the system.
Please refer also to this interesting discussion.Requirement: Powershell
SO: Windows 10
-
-
If you use other methods to get the installation date, please share them in the comment box.

![[Note] Drive acquisition using dc3dd](https://www.forensics-matters.com/wp-content/uploads/2018/07/analogue-business-close-up-117729-825x510.jpg)